Filter News

Raysync News
February 21, 2024Raysync Cloud: A High-Speed File Transfer Cloud Service
High-speed file transfer cloud service - Raysync Cloud is newly launched!

5 Small Business File Transfer Solutions
The needs of small & medium business for file transfer cannot be ignored. This article lists 5 tools of file sharing for SMB, if you want to know more you can click!

User Guide
December 15, 2022Raysync Released New Function: File Sharing Download Link Binds the First Device
The administrator can check the user who created the shared link, link share time, expired time, whether bind to the first device or not, and the device ID that binds as the first device.

An Signiant Alternative for Enterprise
Signiant alternatives are a way for enterprises to solve transfer problems, including transfer speed, data distribution, and security that should not be overlooked. This article lists other tools to replace signiant, click to learn more!

Raysync News
December 14, 2022How to Customize Media Trends with Quick File Transfer Tool
Media producers have noticed an increase in workload. Each department needs to produce media materials with different stages and huge data volume, and smooth collaboration and effective data migration are needed among departments.

User Guide
December 14, 2022Don't Ignore This "Online Preview" Function When Transmitting Media Files
For film and television production enterprises, media documents are the core assets of enterprises and a stepping stone for enterprises to seek partners.
User Guide
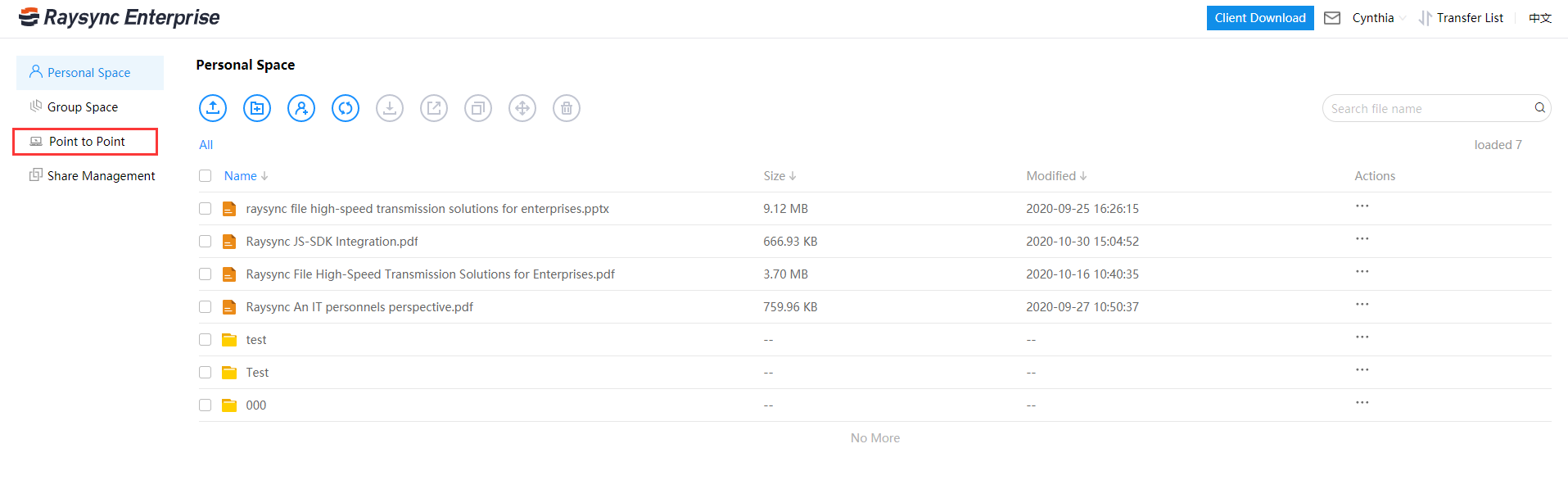
December 13, 2022Application of Raysync Point-to-Point Transfer
Click Start to transfer, one record in the direct transfer file list is one task number, and if multiple records are displayed, it will be regarded as multiple tasks.

Case Studies
December 13, 2022Case Study: Raysync & Outpost Facilities
Outpost distributes the video content to their clients using the accelerated Raysync file transfer protocol. From installation to configuration, the process was quick, simple, and had no downtime.

Case Studies
December 13, 2022Case Study: Raysync & The Monk Studio
With the assistance of Raysync SMB, The Monk Studio delivered the finished film to their clients located worldwide at maximum speed, while ensuring stable and reliable delivery.

How to Centrally Manage Transfer Tasks for Multiple Client Nodes
Enterprises and departments with high transfer needs have lots of data to transfer every day. Raysync's new feature is to centrally manage transfer tasks for multiple client nodes. If you want to learn more, click on this article!