Filter News
Industry news
Industry news
August 29, 2023How to accelerate video file transfer
Video file transfer is increasingly in demand in the film and television industry. Raysync helps the development of file transfer.

Industry news
August 28, 2023How Large File Transfer Acceleration Solutions Empower the Development of Cloud XR Applications
This article will introduce the role and significance of large file transfer acceleration solutions in empowering the development of cloud XR applications. Let us explore together.

Industry news
August 25, 2023Several Technical Solutions for Accelerating Data Transfer
The speed of data transfer can determine the efficiency and cost of data processing. Accelerating data transfer has become a focal point for many businesses and organizations.
Industry news
August 24, 2023What is UDP Protocol and UDP-based Data Transfer Protocol?
UDP is a connectionless transport layer protocol and part of the TCP/IP protocol suite. UDP is known for its high transfer efficiency and is suitable for data transfer scenarios with high real-time requirements.
Industry news
June 9, 2023How to Secure Cloud Storage Data with Raysync
Raysync's Secure File Transfer Service has implemented a series of security control measures that enhance data communication when connecting to cloud resources and calling APIs.

Industry news
February 8, 2023Get Rid of These Two Misconceptions and Be Alert to Unsafe Data Transfer
The amount of data generated by companies is increasing. Enterprises hope that data can guide business decision-making. Companies pay more and more attention to data, and more and more data are stored in the cloud.

Industry news
February 8, 2023How does File Sharing Bring Data Security Threats in Enterprises?
However, when employees pursue speed and shorten workflow, they often ignore the file-sharing security problems brought about by data movement, thus leading the enterprise security situation to an uncontrollable situation.

Industry news
February 8, 2023Practical Functions Update of Raysync Cloud Premium Plan
If you enable the Download with login option, the download traffic produced by the link receiver you share will directly be deducted from your account.
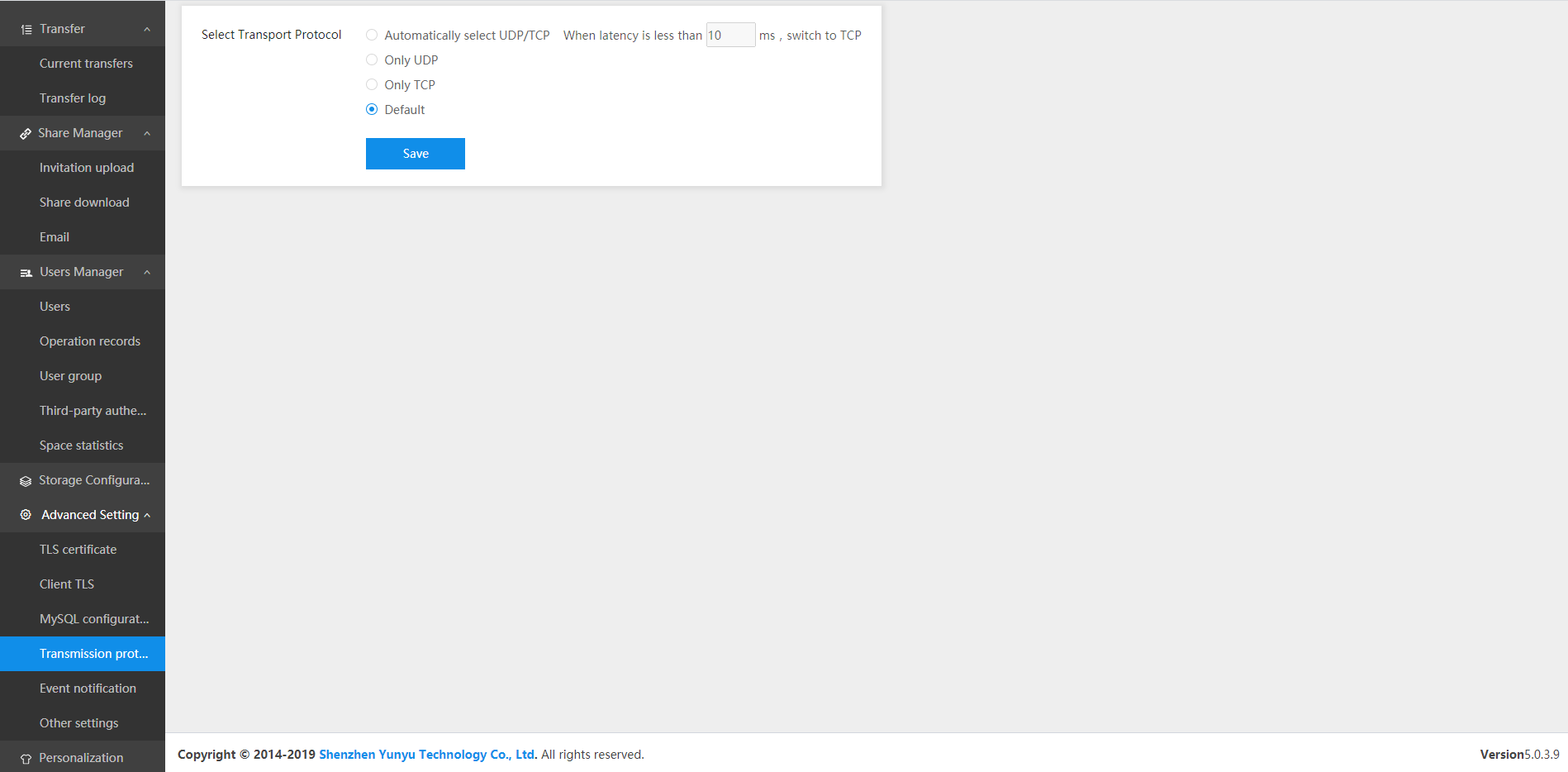
Industry news
February 2, 2023Raysync Large File Transfer: How to Choose File Transfer Protocol?
In the process of file transfer, TCP and UDP are transport layer protocols, and their communication mechanisms are different from the application scenarios. The version V5.0.3.8 of Raysync supports the setting of transfer protocol in 4.