Filter News
User Guide

User Guide
February 23, 2021Powerful Storage Function Does Raysync Large File Transfer System Own
Split a file into individual data blocks, and then store these blocks as separate data. Each piece of data has a different address, so there is no need to store them in a file structure.
User Guide
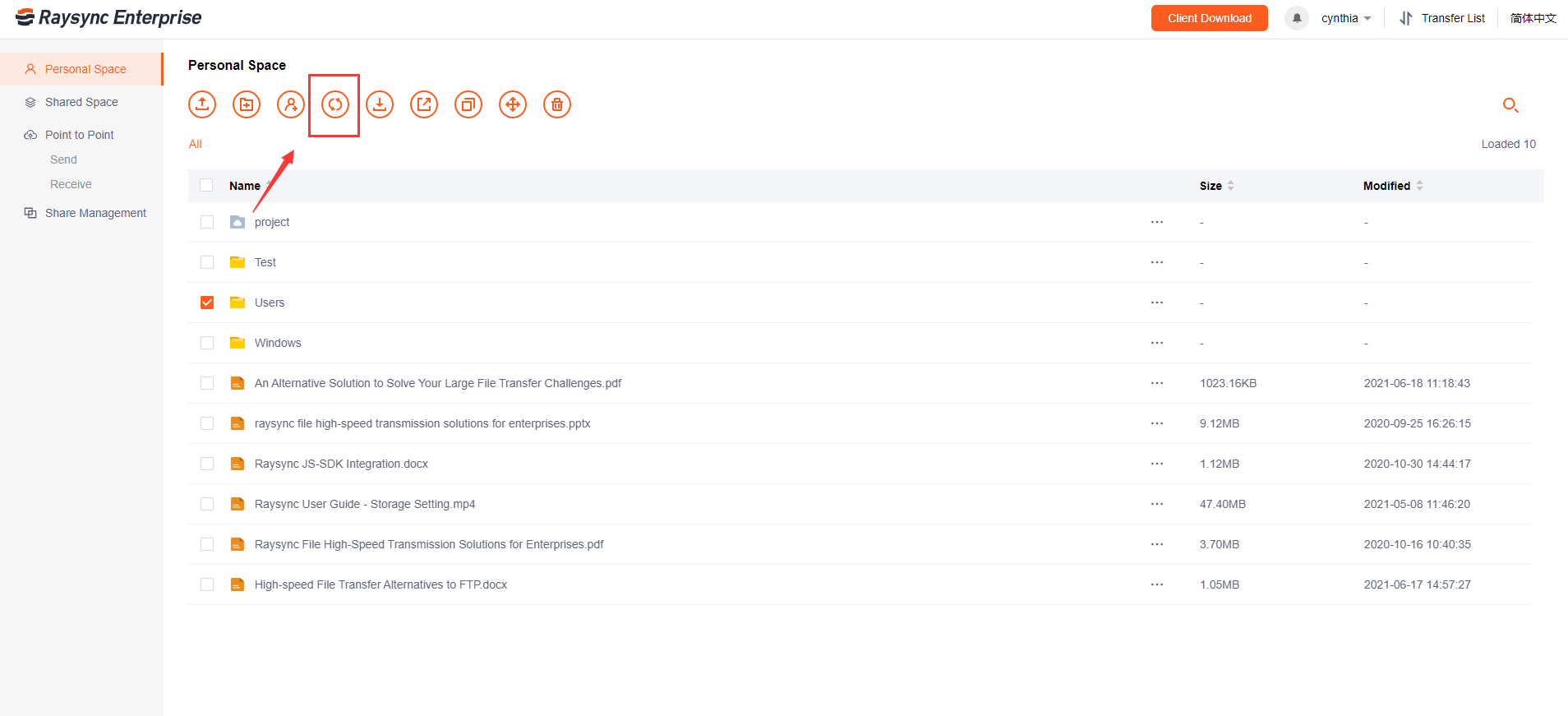
January 27, 2021Tutorial: How Does the Raysync File Sync Function Work?
File synchronization software is used to store copies of on-premises data to another device or to the cloud. The files are typically available to be accessed via a Web-based portal.
User Guide
December 29, 2020Ultimate Guide: how to share Files/Folders
Set email notification: Send the message of sharing the link to the email address of your friends to remind them to open the link to download the file.

User Guide
December 23, 2020Raysync Security Design: Encryption Certificate Life Cycle Management
If the prompt of the certificate is expired shown in the admin console, you need to upload the certificate again to ensure the transfer security.

User Guide
December 15, 2020Raysync Security Design: Behavioral Audit
The Raysync server completely records the complete behavior logs of users logging in, logging out, uploading, downloading, changing passwords, sharing links, etc., and the administrator can regularly audit the user behavior information.

User Guide
December 14, 2020Raysync Security Design: Software Installation
As with some other file transfer software, it takes a few steps to install Raysync including download the installation package, unzip, launch and activate it in three minutes, and then you can easily access the client.
User Guide
December 11, 2020Raysync Security Design: Account&Password Protection
The system provides a weak password dictionary. Users can customize weak passwords that meet the password strength but are easy to be cracked by social engineering.

User Guide
December 9, 2020Raysync Security Design: Web Security
HTTPS TLS 1.1, TLS 1.2, TLS 1.3, only open the encryption algorithm suite recognized by the industry as safe;
User Guide
November 24, 2020Tutorial | How to Receive Files by Using Point to Point Transfer?
The recipient check "Allow to receive direct transfer files from partners" under the Point to Point option, then the Key and ID will display on the left side of the navigation bar.