Filter News
Raysync News
September 11, 2023Raysync, a leading provider of high-performance file transfer solutions, has announced a strategic partnership with Red Hat, the world-renowned open-source software and solutions provider.

You need to copy huge files from your phone to your computer. If the file is too large to be directly transferred via email, cable or other conventional methods, how can I get the large file on the computer?

Q&A
May 11, 2021File Transfer Protocol (FTP) is a server that sends files over the network. Other software available and the way FTP works in the background to ensure correct data transfer.

Raysync News
April 13, 2021What you do when someone asks you to send large files over the internet? This article lists 10 free services to send large files in 2021 that you can refer to it.

User Guide
February 23, 2021Split a file into individual data blocks, and then store these blocks as separate data. Each piece of data has a different address, so there is no need to store them in a file structure.

Q&A
February 22, 2021Point-to-point, multi-point mutual transmission, data cloud transmission, one-to-many data distribution, and other modes are often needed in enterprise offices, but there are few large file transmission tools that can really meet the above requirements.

Raysync News
January 28, 2021Based on UDP, Raysync ultra-high-speed transmission protocol breaks through the technical barriers of traditional transmission protocols, and the transmission speed is increased to 100 times that of FTP.
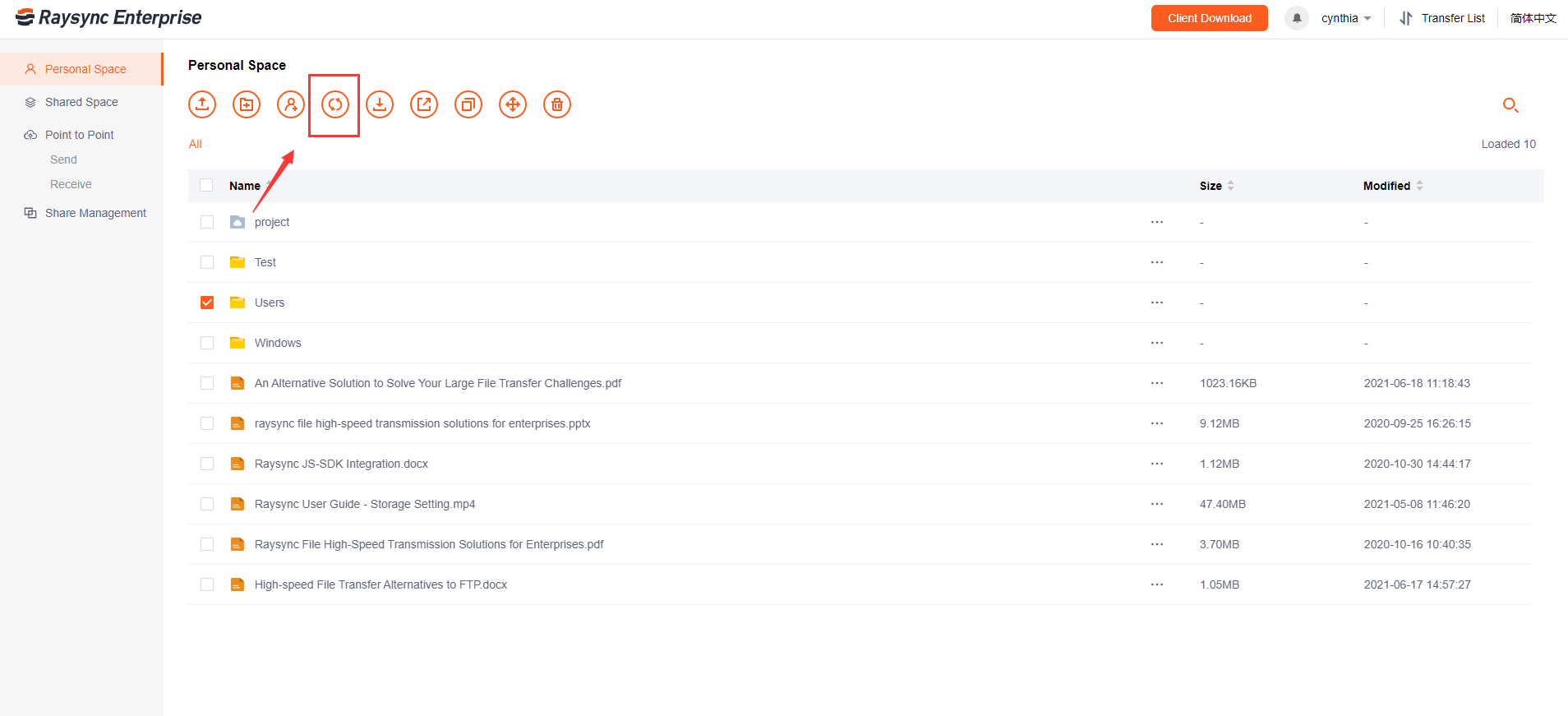
User Guide
January 27, 2021File synchronization software is used to store copies of on-premises data to another device or to the cloud. The files are typically available to be accessed via a Web-based portal.
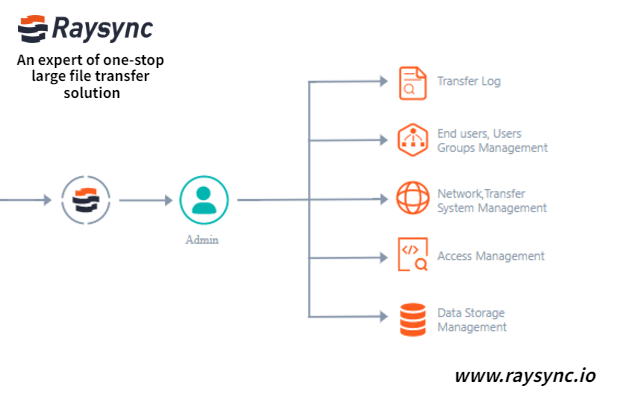
Raysync News
January 12, 2021Support local storage and three-party cloud object storage, with its own configuration and flexible switching;

User Guide
December 23, 2020If the prompt of the certificate is expired shown in the admin console, you need to upload the certificate again to ensure the transfer security.