Why Watermarking Is Essential for Enterprise Digital Asset Protection
October 21, 2025.png)
In today's digital-first world, a company's most valuable assets are often its digital files—from product designs and marketing photos to confidential videos and proprietary documents. Managing and protecting these assets is paramount. This is where digital watermarking becomes an indispensable tool for any enterprise serious about its Digital Asset Management (DAM) strategy.
What is Watermarking in the Context of Enterprise DAM?
Watermarking refers to embedding a recognizable mark—either visible (such as a logo or text) or invisible (embedded metadata or robust signal-level mark)—into a digital asset (image, video, document) to identify ownership, rights information or distribution intent.
Within enterprise DAM systems, watermarking often integrates with workflows that manage, store, distribute and track assets. For example, Adobe Experience Manager Assets supports adding an image‐based watermark to assets automatically.
Watermarks serve multiple purposes: branding (making sure assets are attributed to the enterprise), rights assertion (identifying who owns or authorised the content), traceability (tracking where the asset goes) and deterrence (making unauthorised use less attractive).
The Importance of Watermarking in Enterprise Security
Watermarking serves multiple crucial functions within an enterprise environment, directly addressing the challenges of asset security, brand control, and IP protection. When managed correctly, it transforms a simple file into a trackable, protected corporate asset.
1. Deterring Piracy and Unauthorized Use
The most apparent benefit of watermarking is its power to deter theft. A visible watermark—like a company logo or a "Confidential" stamp—acts as a clear and immediate deterrent. It signals that the asset is proprietary and not for public use. Potential pirates are less likely to steal an asset that is clearly marked, as it cannot be easily repurposed or claimed as their own.
For instance, a photography studio sharing a preview gallery with a client would apply a prominent watermark to each photo. This allows the client to review the images without being able to use them commercially until they have purchased the final, unwatermarked versions. This simple step prevents the unauthorized circulation of pre-release or un-purchased assets.
2. Proving Ownership and Protecting Intellectual Property
What happens when an asset is stolen despite deterrents? This is where invisible watermarks come into play. Using a technique called steganography, data such as the creator's ID, the date of creation, or transaction details can be embedded directly into the file's data. This digital signature is imperceptible to the naked eye but can be read by specialized software.

If a company finds one of its proprietary images or videos being used without permission on another website, an invisible watermark provides undeniable proof of ownership. This forensic evidence is invaluable in legal disputes, copyright claims, and Digital Millennium Copyright Act (DMCA) takedown notices. It serves as a digital fingerprint, definitively linking the asset back to its rightful owner.
3. Streamlining Digital Asset Management (DAM)
In large enterprises, thousands of digital assets are created, shared, and archived daily. Watermarks can be used to embed crucial metadata that helps streamline this complex process. For example, a watermark could contain information about:
-
Asset Status: Draft, For Review, Approved, Archived
-
Project Code: Linking the asset to a specific campaign or department
-
Usage Rights: Internal Use Only, Limited Distribution, Public Release
This embedded information helps DAM systems and employees quickly identify the status and permitted use of an asset, reducing the risk of accidental misuse and improving overall workflow efficiency. It ensures that only the correct version of an asset is used in the right context.
Integrating Watermarking with Secure File Transfer
Protecting digital assets requires a two-pronged approach: securing them at rest (in storage) and in transit (during transfer). While watermarking secures the asset itself, it’s equally important to ensure the file's journey is protected. This is where a secure and efficient file transfer solution becomes critical.
A robust DAM strategy is incomplete if assets are transferred using unsecured, slow, or unreliable methods. Sending large, high-value digital files—such as 4K video footage or high-resolution design files—requires a solution that can handle the size and guarantee security.
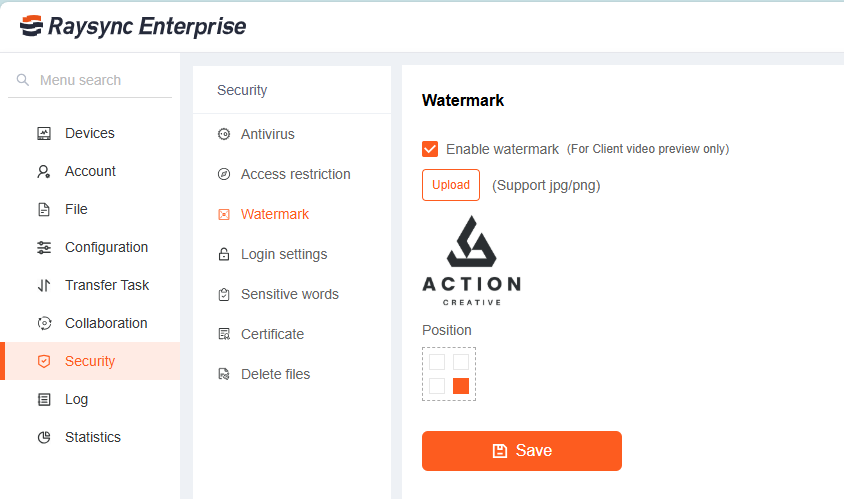
Raysync complements your watermarking strategy by providing a high-speed, secure, and reliable file transfer protocol. By using Raysync to share watermarked assets with clients, partners, and internal teams, you ensure:
-
End-to-End Encryption: Your assets are protected from interception during transfer.
-
High-Speed Delivery: Large files are transferred hundreds of times faster than traditional TCP-based methods, ensuring your workflow remains efficient.
-
Access Control: You can manage who sends and receives files, adding another layer of security to your DAM process.
Pairing a strong watermarking policy with a powerful transfer solution like Raysync creates a comprehensive security shield around your digital assets. The watermark protects the file's integrity and ownership, while Raysync ensures its journey from one point to another is safe and swift.
Conclusion
In a nutshell, watermarking is not merely a feature—it is a fundamental pillar of modern digital asset management and IP protection. It deters piracy, proves ownership, and organizes assets. For enterprises looking to build a truly secure ecosystem for their digital content, combining a robust watermarking strategy with a secure, high-speed file transfer solution like Raysync is the definitive path forward.
You might also like

Industry news
April 17, 2025Considering OneDrive for Business? Our in-depth purchasing guide offers a human-friendly review, highlighting key features, pricing, and benefits. Make an informed decision before you buy.

Industry news
September 27, 2024Discover how FileCatalyst Transfer Agent accelerates file transfers over remote networks. Explore its key features, download process, and consider Raysync as a potential alternative.

Industry news
November 1, 2024Looking for a seamless file transfer experience on Mac? Check out our list of the top 5 equivalents for WinSCP on Mac. Compare features, pricing, and user reviews to make an informed decision.